Demartek Commentary - There’s Spam in Them Thar Clouds
29 August 2014
By Dennis Martin, Demartek President
With all the hype associated with “cloud computing,” I decided to do some testing of the world’s public cloud infrastructure over the past few days. I was not trying to boil the ocean, but had a very specific hypothesis and set of tests in mind.
Conventional wisdom suggests that unsolicited commercial email (UCE), also known as spam, originates from compromised computers all over the world, and I have every reason to believe that spammers use this technique. My hypothesis, however, is that public cloud infrastructure is a major source, and possibly the largest source of spam on the Internet.
These days, basic cloud computing resources are available at very low cost from a variety of cloud providers. Many of the computing product vendors are building and selling cloud computing platforms that include various combinations of server, network, and storage hardware and software. For spammers, cloud computing advantages include pristine platforms, 24x7 uptime, business-class Internet bandwidth and a range of static IP addresses. Public cloud infrastructure is the computer industry’s gift to spammers.
Here’s how it works. A spammer can rent enough cloud computing resources from multiple cloud providers to send large amounts of spam for a few minutes, hours, days or weeks using their own money or with a stolen credit card. These cloud resources start from a clean slate with no operating system, so the spammer does not have to hack into other computers to create a zombie botnet. The spammer can install its spamming application and operating environment and send spam at a rate just below the threshold that the service providers might notice (either in bursts or total amount of messages) until the spam complaints and credit card fraud complaints start arriving. The spammer then closes the account (or the cloud provider closes it) and moves on to another cloud provider. The cloud providers certainly have legitimate business customers who are not spammers, and it can be difficult to weed out the spammers. If the spamming organization does well enough, it can become its own cloud provider and offer cloud computing resources to other businesses (including other spammers) while allocating some of the cloud resources to its own spamming operation.
 Email spam legislation has been passed in many countries. Sending spam from those countries can be considered
criminal activity, and is frequently associated with organized crime. There are several good reports
describing some of this activity. The Internet Crime Complaint Center (IC3) Annual Reports provide a good
description of the kinds of fraud attempts attempted via the Internet, many of them sent through spam email.
Symantec publishes annual and monthly Internet Security Threat Reports that highlight a great deal of attempted
Internet fraud, including email spam. Sophos publishes their quarterly “Spampionship” report that lists the
countries sending the most spam.
Email spam legislation has been passed in many countries. Sending spam from those countries can be considered
criminal activity, and is frequently associated with organized crime. There are several good reports
describing some of this activity. The Internet Crime Complaint Center (IC3) Annual Reports provide a good
description of the kinds of fraud attempts attempted via the Internet, many of them sent through spam email.
Symantec publishes annual and monthly Internet Security Threat Reports that highlight a great deal of attempted
Internet fraud, including email spam. Sophos publishes their quarterly “Spampionship” report that lists the
countries sending the most spam.
I am not the first to draw a connection between spam and public cloud infrastructure, but I decided to test this hypothesis by tracing the sources of all the spam that I received over a few days. Because my primary business email address is public and I have had the same email address for several years, I receive more spam than my colleagues here at Demartek. As a result, I regularly receive a good set of sample data to test.
Like many organizations, we here at Demartek host our own email system on-premise. We get the benefit of having virtually instant access to our email, calendar, contacts, task lists, etc., which help make it easy to get work done and collaborate here in our office. We do not have to share any of our email system resources with other organizations, so we have the most control and flexibility with our system. This also means that we are responsible for our own backup, spam filtering and maintenance of the system. We run Microsoft Exchange Server and have enabled recipient filtering, sender filtering, sender ID filtering, intelligent message filtering and connection filtering in order to reduce the amount of spam that gets to our individual in-boxes and junk mail folders.
The first requirement for my testing was to ensure that our email system was not sending out spam generated by others on the Internet. I verified that our email system was not operating as an open mail relay by using three different publicly available open mail relay test applications. These tests confirmed that our email system successfully prevented all attempts to be used as an open mail relay. Although this is a somewhat older technique for spammers to use, recent reports suggest that some email systems still allow this and that spammers will exploit it if available.
The next phase of the testing involved examining the actual spam messages received. We use Microsoft Outlook as our primary email client, and it disables links and other functions of any email in the junk email folder, making messages in the junk email folder safe to examine. Having examined quite a bit of spam in the past, I have determined that it is nearly impossible to keep up with correct and incorrect spellings of various words, phrases and topics found in these messages. Much has been written on checksums, heuristics, text formatting and other techniques to identify spam based on its contents, and there are several reputable anti-spam products available today that use these techniques.
For this set of tests, my only criteria was the sending IP address and the whether or not the sending IP address was within the range of addresses assigned to a cloud service provider. The sending IP address is in the header of each message, and it is a fairly simple process to determine if a cloud service provider has been assigned that IP address.
There is a class of products known as outbound spam filtering. In my opinion, every cloud service provider and enterprise using a cloud solution (public, private or hybrid) should be using some form of outbound spam filtering. These solutions help cloud service providers, and the businesses that use them, maintain their reputation and avoid getting on the spam blacklists.
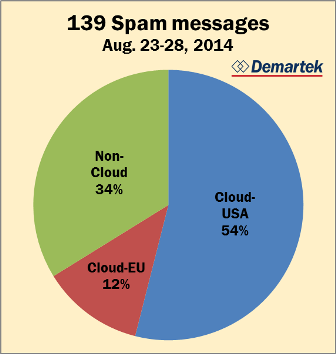 During these few days of testing, I received 139 spam messages that arrived in my junk mail folder. These are the
messages that were able to get past the basic spam checks performed by our email server itself. For purposes of
this test, I did not check the email server system logs to see how many messages were rejected by our email system.
I compared the IP addresses of the sending computers to the IP address ranges allocated to various cloud providers.
The pie chart provides a description of the sources of these emails. Of the 139 spam messages that I received,
two-thirds of them came from IP address ranges clearly identifiable with cloud providers. The majority of
these cloud providers are based in the USA, and several of these appear to be the same cloud provider operating
under different names. A fair number of the spam email messages came from cloud providers based in eastern Europe.
During these few days of testing, I received 139 spam messages that arrived in my junk mail folder. These are the
messages that were able to get past the basic spam checks performed by our email server itself. For purposes of
this test, I did not check the email server system logs to see how many messages were rejected by our email system.
I compared the IP addresses of the sending computers to the IP address ranges allocated to various cloud providers.
The pie chart provides a description of the sources of these emails. Of the 139 spam messages that I received,
two-thirds of them came from IP address ranges clearly identifiable with cloud providers. The majority of
these cloud providers are based in the USA, and several of these appear to be the same cloud provider operating
under different names. A fair number of the spam email messages came from cloud providers based in eastern Europe.
It is possible that some of the virtual systems configured and deployed at cloud hosting sites are legitimate systems that have actually been compromised by spammers. However, the beauty of virtual systems in a cloud environment is that if they are compromised, they can be easily wiped and restored to their pristine state fairly quickly by their legitimate owners. So it seems to me that if large amounts of spam are consistently coming from IP addresses controlled by cloud providers, that it is most likely because the spammers themselves are using cloud hosting services directly.
On one side, we have lots of great technology applied to the automation of sending many millions of email messages. On the other side, we have lots of great technology dedicated to rejecting, blocking, deleting or re-routing these same millions of email messages. I would prefer that we dedicate all this great technology to better causes.


 We are pleased to announce that Principled Technologies has acquired Demartek.
We are pleased to announce that Principled Technologies has acquired Demartek.